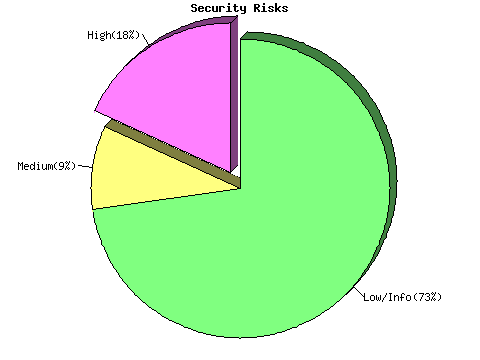

Vulnerability found on port ftp (21/tcp)
Vulnerability found on port ftp (21/tcp)
Information found on port ftp (21/tcp)
An FTP server is running on this port.
Here is its banner :
220 noc.cctld.or.ke FTP server (Version 6.00LS) ready.
Nessus ID : 10330
Information found on port ftp (21/tcp)
Remote FTP server banner :
220 noc.cctld.or.ke FTP server (Version 6.00LS) ready.
Nessus ID : 10092
Information found on port ftp (21/tcp)
Remote FTP server banner :
220 noc.cctld.or.ke FTP server (Version 6.00LS) ready.
Nessus ID : 10092
Information found on port ssh (22/tcp)
An ssh server is running on this port
Nessus ID : 10330
Information found on port ssh (22/tcp)
Remote SSH version : SSH-2.0-OpenSSH_3.8.1p1 FreeBSD-20040419
Remote SSH supported authentication : publickey,keyboard-interactive
Nessus ID : 10267
Warning found on port domain (53/tcp)
The remote name server allows DNS zone transfers to be performed.
A zone transfer will allow the remote attacker to instantly populate
a list of potential targets. In addition, companies often use a naming
convention which can give hints as to a servers primary application
(for instance, proxy.company.com, payroll.company.com, b2b.company.com, etc.).
As such, this information is of great use to an attacker who may use it
to gain information about the topology of your network and spot new
targets.
Solution: Restrict DNS zone transfers to only the servers that absolutely
need it.
Risk factor : Medium
CVE : CAN-1999-0532
Nessus ID : 10595
Information found on port domain (53/tcp)
BIND 'NAMED' is an open-source DNS server from ISC.org.
Many proprietary DNS servers are based on BIND source code.
The BIND based NAMED servers (or DNS servers) allow remote users
to query for version and type information. The query of the CHAOS
TXT record 'version.bind', will typically prompt the server to send
the information back to the querying source.
The remote bind version is : 9.3.1
Solution :
Using the 'version' directive in the 'options' section will block
the 'version.bind' query, but it will not log such attempts.
Nessus ID : 10028
Information found on port domain (53/tcp)
An unknown service runs on this port.
It is sometimes opened by this/these Trojan horse(s):
ADM worm
Lion
Unless you know for sure what is behind it, you'd better
check your system
*** Anyway, don't panic, Nessus only found an open port. It may
*** have been dynamically allocated to some service (RPC...)
Solution: if a trojan horse is running, run a good antivirus scanner
Risk factor : Low
Nessus ID : 11157
Information found on port http (80/tcp)
This port was detected as being open by a port scanner but is now closed.
This service might have been crashed by a port scanner or by a plugin
Nessus ID : 10919